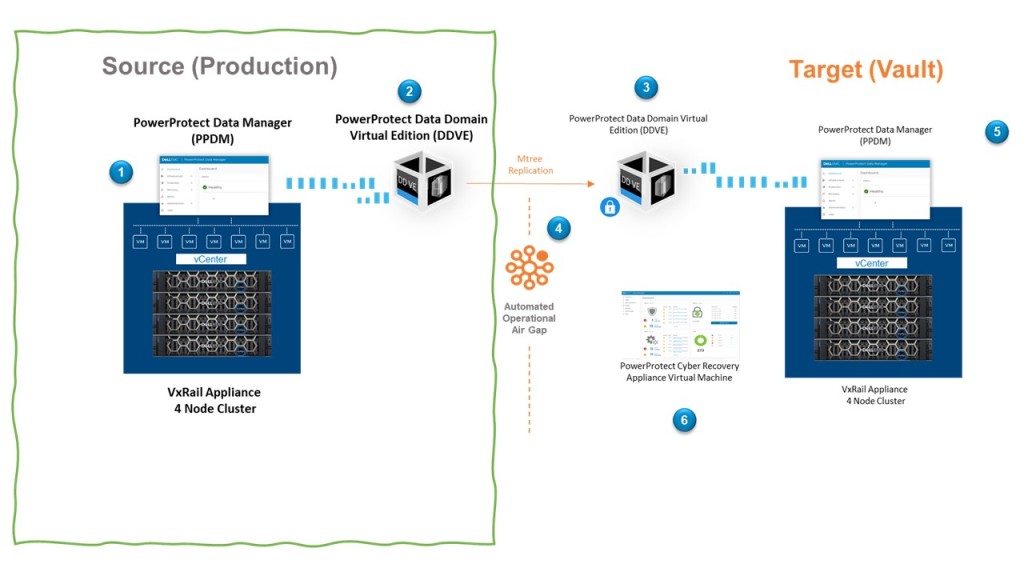
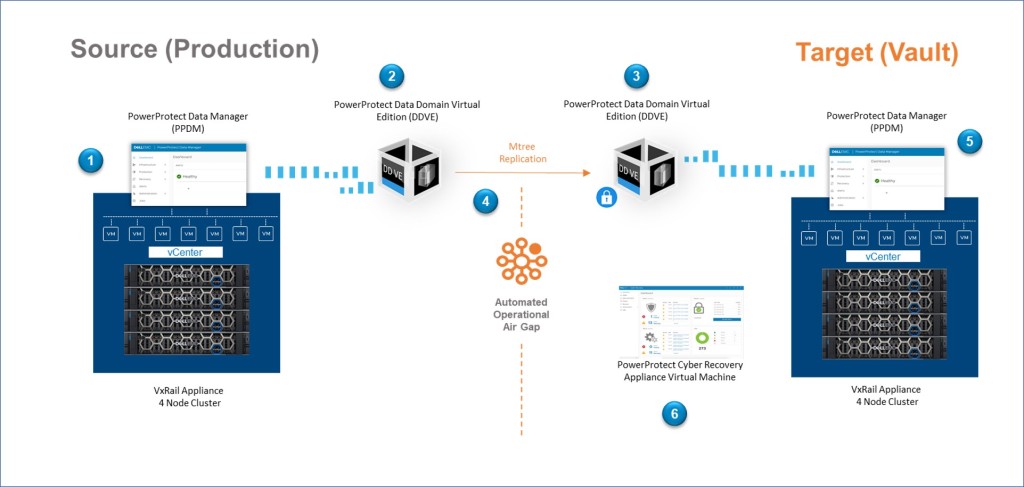
Last week we overviewed the big picture (Diagram Below), and very briefly discussed the end to end flow (Steps 1 through 6) During this post we will start to break this up into consumable chunks and digest in a little more detail. Whether you are deploying the Cyber Recovery solution in one fell swoop or you have already have a data protection architecture leveraging Dell Power Data Protect Manager with Data Domain and you are investigating attaching the vault as a Day 2 activity, then hopefully you will find this post of interest.
Production Side
This post will concentrate on part of the ‘Big Curvy Green Box’ or the left side of the diagram. I am leveraging a VxRail with an embedded vCenter, for a couple of reasons a) I’m lucky to have one in my lab and b) it’s incredibly easy. This has been pre-deployed in my environment. Obviously, if you are following this blog, you can use any host/vCenter combination of your choosing.
This post will focus on how we stand up the Data Domain Virtual Edition appliance, with a view to leveraging this for the Cyber Recovery use-case only. Health Warning – this is for demo purposes only and we will absolutely not be making any claims with regards to best practices or the suitability of this setup for other use-cases. In the spirit of blogging, the goal here is to build our understanding of the concepts.
We will follow up next week to overview the basic setup of PPDM in the Production side and how it integrates with vSphere vCenter and the PowerProtect DDVE appliance.
Sample Bill of Materials Production Side
I’ve been careful here to call out the word sample. This is what I have used for this blog post, of course in production we need to revert to the official interoperability documentation. Just stating the obvious…. :).That being said this is what I have used in my setup.
- VMware ESXi Version 7.0.3 (Build 19898904)
- VMware vCenter Server 7.0.3 00500
- Dell PowerProtect Data Manager 19.11.0-14
- Dell PowerProtect DD VE 7.9.0.10-1016575
Prerequisites
As per the diagram I’m running this on 4 node VxRail cluster, so my TOR switches are setup properly, everything is routing nicely etc. The VxRail setup also configures my cluster fully with a VSAN Datastore deployed, vMotion, DRS, HA, and a Production VDS.
This won’t come as surprise but the following are critical:
- Synchronised Time everywhere leveraging an NTP server
- DNS Forward and Reverse lookup everywhere.
In some instances during installation you may be given the option to deploy devices, objects etc., leveraging IP addresses only. My experience with that approach isn’t great so DNS and NTP everywhere are your friend.
Assumptions
As per my previous post, I’m going to attempt brevity and to be as concise as possible. For partners/Dell employees reading this, then you will have access to more of the in-depth guidance. I urge everybody to familiarise themselves with the documentation if possible.
I’ll publish an ‘end to end’ configuration/demo video at the end of this series. In the interim I like using the ‘Gallery’ and ‘Images’ so readers can pause and review in their own time.
Some Lower Level Detail
The following is the low-level setup, which should help guide through the screengrabs.
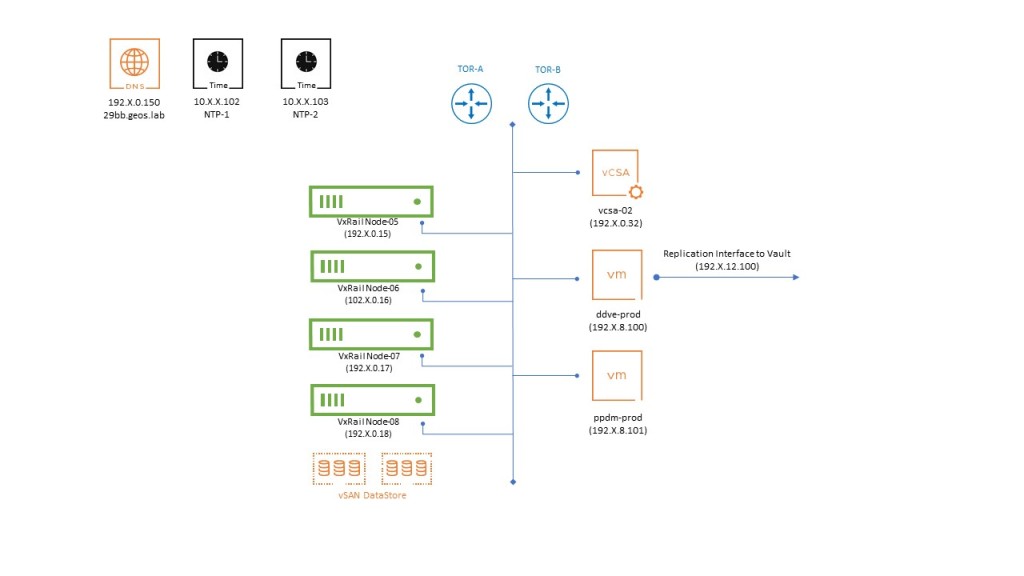
This is all very straightforward. We have:
- Our 4 VxRail Nodes with a vSAN Datastore pre-built.
- Embedded VxRail vCenter server pre-deployed on the first host.
- VMware Virtual Distributed Switch (VDS) with ESXi Management, vMOTION and a couple of other networks provisioned.
- Routing pre-configured on two Dell TOR switches. Some very basic routing between:
- The internal VxRail networks (Management, vMotion, and some other Managment networks we have provisioned)
- Reachability to the Vault network via a Replication interface (More on that in a while)
- Reachability to the IP services layer (DNS & Redundant NTP servers)
- DNS forward and reverse lookup configured and verified for all components.
Step 1: Deploy PowerProtect DDVE
First step is to download the PowerProtect DDVE OVA from the Dell Data Domain Virtual Edition support site (you will need to register). Here you will also have access to all the official implementation documentation. As ever I urge you to refer to this, as I will skip through much of the detail here. I’m making the bold assumption we know how to deploy OVF’s etc. We will capture the process as mentioned in the wrap up video.
During the OVA setup you will be asked what configuration size you wish. This is a demo so go for the smallest 8TB -2CPUs, 8GB Memory.

The OVA setup will also ask you to select the destination networks for each source network or NIC. This is important as we will leverage the first for the ‘Management network’ and the second as the ‘Replication Network’ as per the previous diagram. In my setup I am using VLAN 708 for Management and VLAN 712 for the DD Replication Network.

Skip through the rest of the OVA deployment. We will deploy on the default VSAN datastore and inherit that storage policy. Of course we have everything else deployed here also, which clearly isn’t best practice but this is of course a demo!
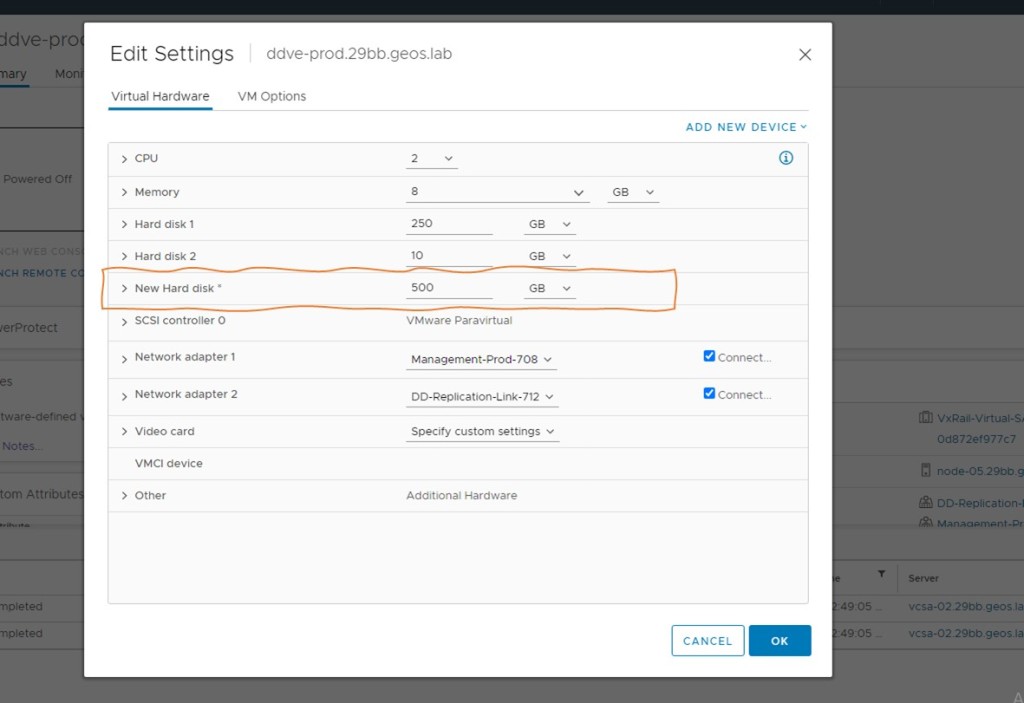
Once the OVA has deployed successfully, do not power on just yet. We need to add target storage for replication. You can get by with circa 250GB, but I’m going to add 500GB as the 3rd hard disk. Right click in the VM, Edit Settings and ‘Add New Device’.
At this point you can power on the VM, open the web console and wait. It will take some time for the VM to initialise and boot. once booted you will be prompted to logon. Use the default combination of sysadmin/changme (you will be immediately prompted to change the password)
By default, the management NIC will look for an IP address via DHCP. If you have a DHCP service running, then you can browse to the IP address and run the setup from there. Of course in most instances, this won’t be the case and we will assign IP addresses manually. I’m going to be a little ‘old skool’ in any regard, I like the CLI.
- Tab through the E-EULA and enter your new password combination, my demo will use Password123!. Incredibly secure I know.
- Answer ‘Yes’ when asked to create a security officer. pick a username, I am using ‘crso’. the password needs to be different from your newly created sysadmin password.
- Answer ‘no’ when prompted to use the GUI.
- Answer ‘yes’ when asked to configure the network.
- Answer ‘no’ when asked to use DHCP.
- Follow the rest as prompted:
- Hostname – your full FQDN
- Domainname
- ethV0 (used for Management)
- eth V1 (we will use for replication to the vault)
- Default Gateway (will be the gateway of ethV0)
- IPv6 – Skip this by hitting return
- DNS Servers
- You will be presented with the summary configuration, if all good then ‘Save’.
- When prompted to configure e-licenses, type ‘no’. we will be using the fully functioning 90 day trial
- When prompted to ‘Configure System at this time’ – type ‘no’
- You will then be presented with a message, ‘configuration complete’
Step 2: Initial Configuration of DDVE
Now browse to the DDVE appliance via the FQDN you have assigned. This should work if everything is setup correctly.
Logon using sysadmin and the password you created earlier.
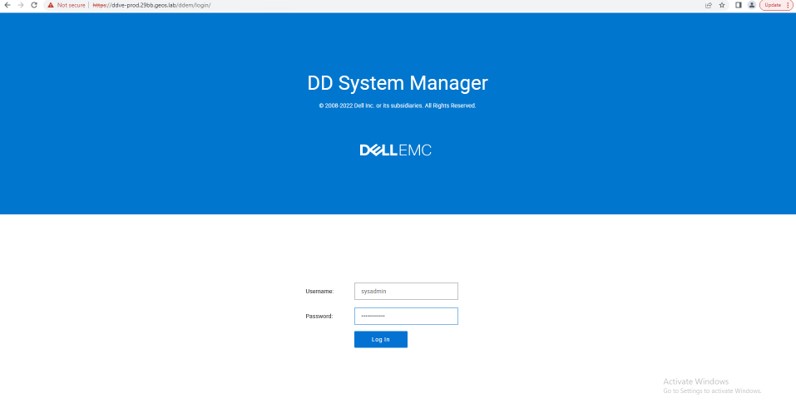
You will be presented with a screen similar to the following. At this point we have no file system configured.
Note: There is a 6 step wizard we could have initiated earlier, but for for the purposes of the Cyber Recovery Demo, it is helpful to get a ‘look and feel’ of the DDVE interface from the start. This is just my preference.
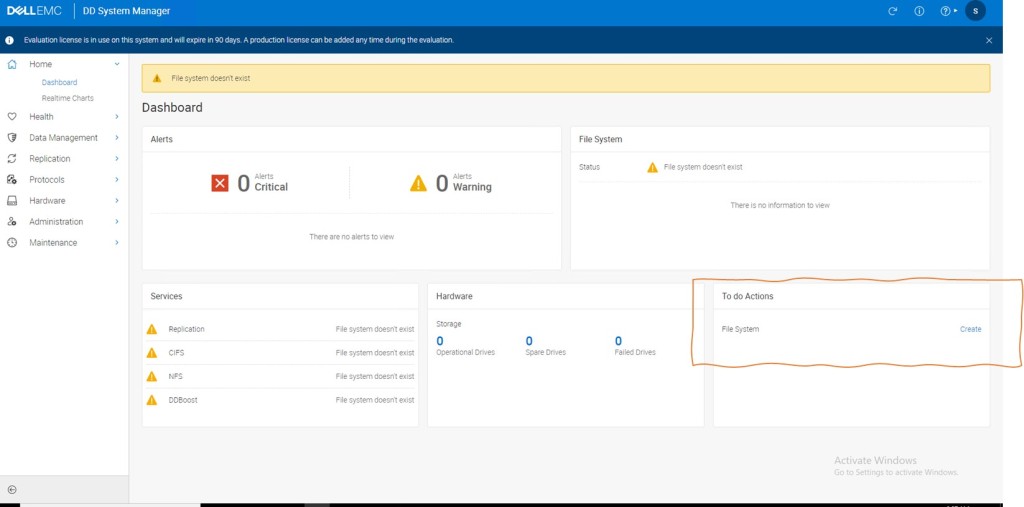
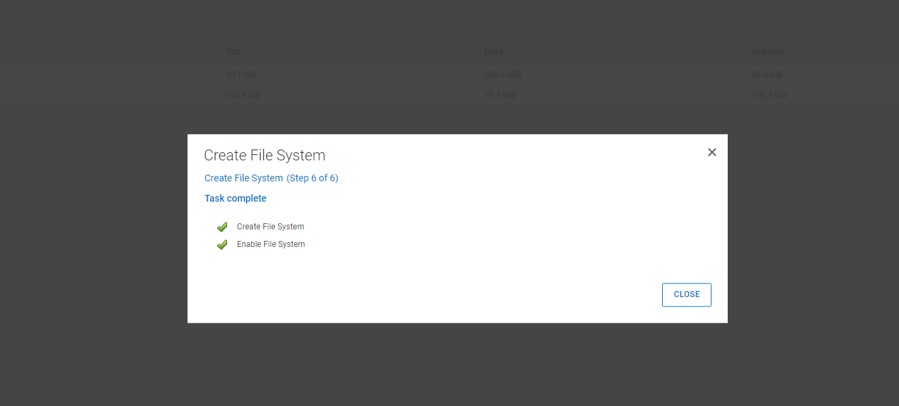
Follow the wizard on screen to create the file system, when presented with the ‘cloud tier’ warning, click next and ignore. Click ‘SKIP ASSESMENT’ in step 4, and then click ‘Finish’. Step 6 will take some time process.
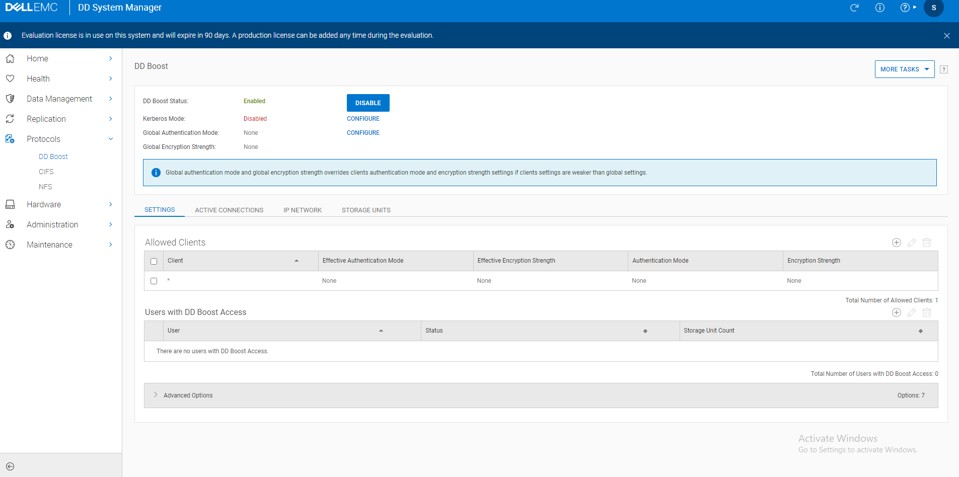
Enable DD Boost and Add User
We need to enable the DD Boost Protocol to make the deduplication process as efficient as possible and implement client side offload capability. We will see where that fits in during a future post.
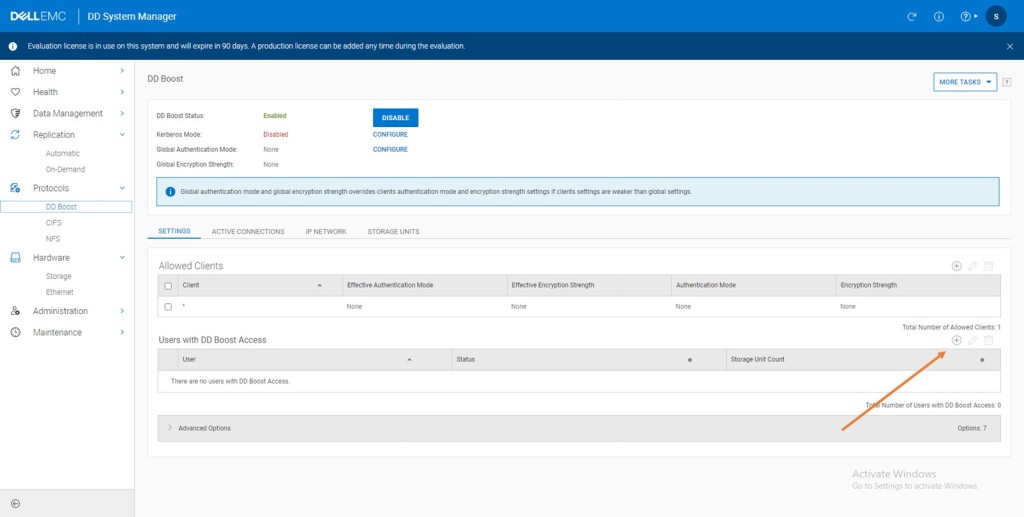
Navigate to Protocols -> DD Boost and Click Enable
We want to add DD Boost user with Admin rights. Firstly create the user by navigating to Administration -> Access -> Local Users -> Create
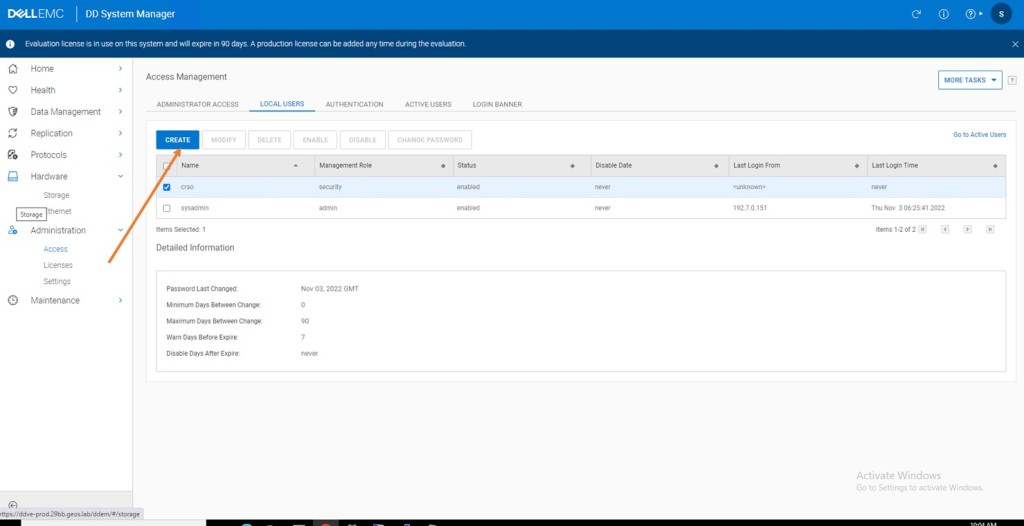
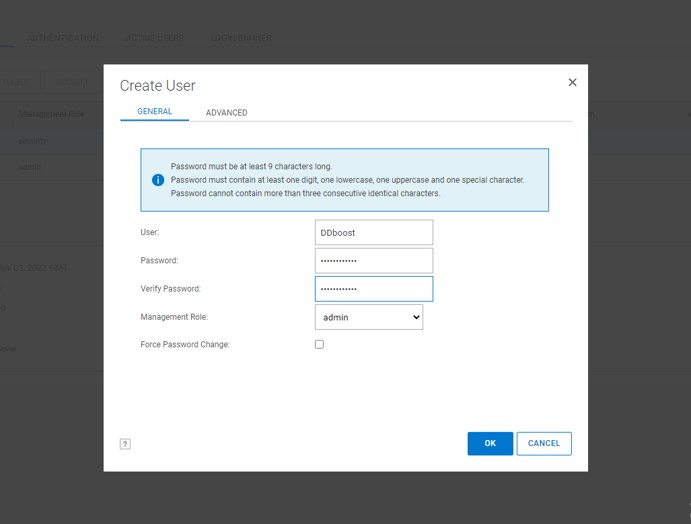
Add this newly created user as a user with DD Boost Access. Follow the workflow and ignore the warning that this user has Admin access.
Wrap Up
So there you have it, a quick overview of our demo environment and we have stood up the Production side DDVE appliance, with a very basic configuration. In the next post we will stand up the production side PowerProtect Data Manager and knit these two components with vCenter.
As mentioned earlier I have skimmed through quite a bit of detail here in terms of the setup. The end goal is for us to dig deeper into our understanding of the Cyber recovery solution proper. So the above is no way representative of best practice as regards DDVE design (the DD storage is on the same VSAN Datastore that the DDVE VM and the machines it protects reside upon for instance ! Definitely not best practice).
For best practice always always refer to Dell official documentation
Thanks for taking the time to read this, and if you have any questions/comments, then please let me know
Cheers
Martin
DISCLAIMER
The views expressed on this site are strictly my own and do not necessarily reflect the opinions or views of Dell Technologies. Please always check official documentation to verify technical information.
#IWORK4DELL







[…] Storage Direct introduced in Release 19.17. I blogged about this feature back in late July. Click here to view…